1.5 研究内容和组织结构
网络安全态势感知包括觉察(Perception)、理解(Comprehension)和预测(Prediction)三个阶段,通过定性或定量的网络安全评价体系对底层各类安全事件进行归并、关联和融合处理,并将获取的态势感知结果以可视化图形提供给网络安全管理员。网络安全态势评估是态势感知的核心,是对网络安全状态的定性定量描述。本书描述了网络安全态势评估体系的基本模型,重点对相关的评估方法做了研究。
本书首先介绍了基于隐马尔可夫模型(Hidden Markov Model,HMM)的态势评估技术。将系统的安全状态、入侵报警事件分别与HMM的状态和观察符号相对应,给出了一种基于HMM的网络风险评估模型。该模型通过关联分析入侵检测系统产生的报警序列,计算各个主机的风险指数,进而对整个网络系统的风险状态进行定量评价。网络风险指数的计算方法简单,速度快,实验结果表明,该模型能够有效对网络系统的安全状态进行定量评估。
然后用隐半马尔可夫模型(Hidden Semi-Markov Model,HSMM)来模拟网络系统的实际运行,以网络防御系统捕获的报警数据作为研究数据源,实现对网络安全态势的评估。因为实际收集到的观测数据可能在同一个状态上发生无规律的驻留,HSMM修改了HMM模型关于系统在某个状态的驻留时间服从指数分布的假定,更适合于描述网络系统运行的实际情况。我们针对系统驻留时间的不同概率分布情况,分别选取了对数分布、负二项分布、几何分布和泊松分布进行了实验测试。其中系统状态驻留时间呈泊松分布时的安全态势评估结果反映了网络攻击的真实情况,黑客发起攻击前先进行探测,经过一段时间的休战,再进行攻击尝试,在黑客的持续攻击下,系统被攻破,实验结果与实际观测结果相吻合。同时,结合HSMM的前向-后向算法,给出了部分观测条件下的HSMM系统状态预测算法,将其应用于Honeynet网络安全态势评估中,得到了较好的评估效果。实验结果表明,由于HSMM可以对系统状态的驻留时间进行建模,非常适合于攻击情况复杂多变的网络系统的安全评估。
从博弈论(Game Theory)的观点来看,信息安全实际上是信息保护者(防御方)与入侵者(攻击方)之间的博弈。本书从博弈论的视角研究信息安全问题,建立了信息安全攻防博弈模型,提出了一种基于随机博弈模型的网络安全量化评估算法。利用安全管理员对网络设备的重要性评定来确定博弈参数,进行纳什均衡(Nash Equilibrium)分析,求得攻防双方的纳什策略(Nash Policy),从而获知网络处于不同安全状态的概率分布,最后可求出网络安全态势量分评估结果。本书提出的攻防双方的博弈模型,为解决现实中的信息安全问题提供了一种新的思路。
本书共分为六章,如图1.6所示,各章的内容安排如下。
第1章简要介绍网络安全技术的发展以及网络安全态势感知中的关键技术,并对论文的研究背景、研究现状和研究意义作了介绍,给出了本书的主要研究内容和组织结构。
第2章介绍网络安全态势感知基础知识,首先介绍了网络安全态势感知研究中所涉及的一些重要概念,给出了态势感知的模型框架和概念模型,并对本领域的主要研究内容作了简述。
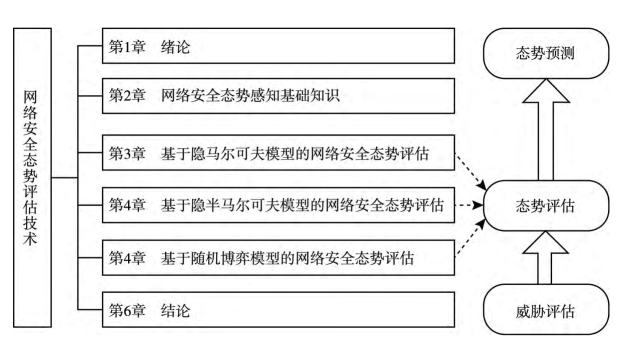
图1.6 本书组织结构
第3章介绍基于隐马尔可夫模型的网络安全态势评估方法。首先介绍了隐马尔可夫模型的相关概念,然后介绍网络安全态势的HMM建模方法,之后进行了实验测试,并对结果进行了评述。
第4章讨论基于隐半马尔可夫模型的网络安全态势评估方法。首先介绍了隐半马尔可夫模型定义,给出HSMM在实际应用中的三个基本问题的解决算法,并对其进行了改进,对核心算法进行了编程实现。其次给出了态势评估模型框架,重点研究了HSMM中状态驻留时间的特点,讨论了在获得部分观测信息后,对系统下一步状态的预测。最后对系统进行了实验测试。
第5章提出基于随机博弈模型的网络安全态势评估方法。介绍了博弈模型要素,建立了攻防博弈的一般模型,以随机博弈为例对网络攻防建模,以HoneyNet数据集为实验数据集进行了实验测试。
第6章给出本书结论,总结了本书提出的态势评估的相关技术,分析相关技术的不足,并对后续的研究工作进行展望。
【注释】
[1]Chen L C,Carley K M.The Impact of Countermeasure Propagation,on the Prevalence of Computer Viruses[J].IEEE Transactions on Systems Man and Cybernetics Part B-Cybernetics,2004,34(2):823-833.
[2]CERT.http://www.cert.org.2011-3-1.
[3]Symantec Corporation.Symantec Internet Security Threat Report,Volume IX,2006.http://eval.symantec.com/mktginfo/enterprise/white_papers/ent_white paper_symantec_internet_security_threat_report_ix.pdf.
[4]沈昌祥.信息安全工程导论[M].北京:电子工业出版社,2003:23-28.
[5]ISS.Internet Security System[EB/OL].http://www.iss.net.2011.
[6]SATAN.Security Administrator Tool for Analyzing Networks[EB/OL].http://www. procupine.org/satan.2011.
[7]Nmap[EB/OL].http://nmap.org.2011.
[8]Nessus[EB/OL].http://www.nessus.org/nessus/.2011.
[9]X-Scan[EB/OL].http://www.xfocus.net/tools/200507/1057.html.2011.
[10]周晓俊.网络渗透测试系统研究[A]//第十六届全国抗恶劣环境计算机学术年会论文集[C].2006:283-288.
[11]文伟平.恶意代码机理与防范技术研究[D].中国科学院软件研究所博士学位论文,2004:17.
[12]Cohen F.A Short Course on Compter Viruses[M].New York:John Wiley&Sons,1994:18-26.
[13]Symantec.Plymorphic Virus Detection Module[M].United States Patent,2004:44.
[14]Arnold W,Tesauro G.Automatically Generated Win32 Heuristic Virus Detection[J].Proceedings of the 2000 International Virus Bulletin Conference,2000:484-495.
[15]Gordon L A,Loeb M P,Lucyshyn W,Rchardson R.2006 CSI/FBI Computer Crime and Security Survery[R].Computer Security Institute Publications,2005.
[16]Keith E.Strassberb,Richard J.Gondex,Gary Rollie.防火墙技术大全[M].北京:机械工业出版社,2003:162-182.
[17]Anderson J P.Computer Security Threat Monitoring and Surveillance[R].Fort Washington, Pennsylvania,1980:9.
[18]Denning D E,Neumann P.G.Requirements and Model for IDES—A Real-Time Intrusion Detection System[R].Computer Science Laboratory,SRI International,Menlo Park,CA,1985:21.
[19]Julisch,K.Mining Alarm Clusters to Improve Alarm Handling Efficiency[J].Proceedings of the Annual Computer Security Applications Conference,New Orleans,LA,2001:19.
[20]Goodall,J.R.,Lutters,W.G.,Komlodi,A.The Work of Intrusion Detection:Rethinking the Role of Security Analyst[J].Proceedings of the Tenth Americas Conference on Information Systems,New York,2004:492-499.
[21]范红,吴亚非,李京春等.信息安全风险评估指南[S].北京:中国标准出版社,2007:44-45.
[22]Ammann,P.,Wijesekera,D.,Kaushik,S.Scalable,Graph-based Network Vulnerability Analysis[J].Proceedings of 9th ACM Conference on Computer and Communications Security.Washingtion,DC,2002:148-160.
[23]张涛,胡铭曾,云晓春等.计算机网络安全性分析建模研究[J].通信学报,2006,26(12):100-109.
[24]张永铮,方滨兴,迟悦.用于评估网络信息系统的风险传播模型[J].软件学报,2007,18(1):137-145.
[25]肖道举,杨素娟,周开锋等.网络安全评估模型研究[J].华中科技大学学报(自然科学版),2002,30(4):37-39.
[26]冯登国,张阳,张玉清.信息安全风险评估综述[J].通信学报,2004,25(7):10-18.
[27]李涛.网络安全概论[M].北京:电子工业出版社,2004:56-68.
[28]Llinas J,Hall D L.An Introduction to Multi-sensor Data Fusion[C].Proceedings of the 1998 IEEE International Symposium on Circuits and Systems,Monterey,CA,USA.1998(6):537-540.
[29]Hall D L,Llinas J.A Challenge for the Data Fusion Community I:Research Imperatives for Improved Processing[C].Proceedings of the 7th National Symposium on Sensor Fusion,Albuquerque,NM,1994:159-175.
[30]Waltz E,Llinas J.Multi-Sensor Data Fusion[M].Boston,MA:Artech House,1990:155-165.
[31]Hall D L.Mathematical Techniques in Multi-sensor Data Fusion[M].Boston,MA:Artech House,1992:66-76.
[32]Hall D L,Llinas J.Handbook of Multi-sensor Data Fusion[M].Washington,NY:CRC Press,2001:123-133.
[33]Steinberg A N,Bowman C L,White F E.Revision to the JDL Data Fusion Model[C].Proceedings of SPIE Aero Sense,Orlando,Florida,1999(3719):430-441.(https://www.daowen.com)
[34]Christopher J A,Sandara G B,Richard D P,et al.Operationally Critical Threat,Asset and Vulnerability Evaluation SM Framework[R].Pittsburgh,PA:Software Engineer Institue,Carnegie Mellon University,1999:77-79.
[35]Bass T,Roger R.Defense-in-Depth Revisited:Qualitative Risk Analysis Methdology for Complex Network-Centric Operations[C].Proceedings of IEEE Military Communications Conference,McLean,VA,USA,2001(1):64-70
[36]朱亮,王慧强,郑丽君.网络安全态势可视化研究评述[EB/OL].http://www.paper.edu.cn/releasepaper/content/200607-36,2006-7-4.
[37]D'Amico A,Kocka M.Information Assurance Visualizations for Specific Stages of Situational Awareness and Intended Users:Lessons Learned[C].Visualization for Computer Security VizSEC 2005,Minneapolis,MN,USA,2005:302-312.
[38]Roesch,M.Snort-Lightweight Intrusion Detection for Network[J].Proceedings of the USENIX LISA’99 Conference,Seattle,Washington,1999:25-37.
[39]CVE.Common Vulnerabilities and Exposures[EB/OL].http://www.cve.mitre.org/, 2008.
[40]Bugtraq[EB/OL].http://www.securityfocus.com/archive/1,2008.
[41]CVSS.Common Vulnerability Scoring System[EB/OL].http://nvd.nist.gov/cvss.cfm, 2008.
[42]Kruegel,C.,Robertson,W.Alert Verification:Determining the Success of Intrusion Attempts [J].Proc.First Workshop the Detection of Intrusions and Malware and Vulnerability Assessment(DIMVA 2004),Dortmund,Germany,2004:186-195.
[43]Deraison,R.Nessus Vulnerability Scanner[EB/OL].http://www.nessus.org/,2008.
[44]Porras,P.A.,Fong,M.W.,Valdes,A.A Mission-Impact-based Approach to INFOSEC Alarm Correlation[J].Poceedings of the 5th International Symposium on Recent Advances in Intrusion Detection(RAID2002).Zurich,Switzerland,2002:95-101.
[45]Koike,H.,Ohno,K.SnortView;Visualization Systems of Snort Logs[C].//2004 ACM Workshop on Visulization and Data Mining for Computer Security.Washington DC,USA:2004.143-147.
[46]Danyliw,R.ACID:Analysis Console for Intrusion Databases[EB/OL].http://acidlab.sourceforge.net.2001.
[47]Hariri,S.,Qu,G.,Dharmagadda,T.Impact Analysis of Faults and Attacks in Large-scale Networks[J].IEEE Security&Privacy,2003(1):49-54.
[48]张义荣,鲜明,王国玉.一种基于网络熵的计算机网络攻击效果定量评估方法[J].通信学报,2004,25(11):159-165.
[49]Blyth,A.Footprinting for Intrusion Detection and Threat Assessment[J].Information Security Technical Report,1999,4(3):43-53.
[50]Mehta,V.,Bartzis,C.,Zhu,H.,Clarke,E.,et al.Ranking Attack Graphs[C].Proceedings of the International Symposium on the Recent Advances in Intrusion Detection(RAID 2006).Springer-Verlag,2006:127-144.
[51]Arnes,A.,Valeur,F.,Vigna,G.,Kemmerer,R.A.Using Hidden Markov Models to Evaluate the Risk of Intrusions[C].Proceedings of the International Symposium on the Recent Advances in Intrusion Detection(RAID 2006).Springer-Verlag,2006:145-164.
[52]Sunu Mathew,C.S.,Shambhu Upadhyaya.An Alert Fusion Framework for Situation Awareness of Coordinated Multistage Attacks[C].Proceedings of the Third IEEE International Workshop on Information Assurance(IWIA′05),College Park,MD,USA,2005:95-104.
[53]Holsopplea,J.,Yanga,S.J.,Suditb,M.TANDI:Threat Assessment of Network Data and Information[C].in:Proceedings of SPIE-Defense and Security Symposium,2006(6242):114-129.
[54]吴世忠.基于风险管理的信息安全保障的研究[D]四川大学,2002:22.
[55]Chinchani,R.,Iyer,A.,Ngo,H.Q.,Upadhyaya,S.Towards a Theory of Insider Threat Assessment[C].Proceedings of the 2005 International Conference on Dependable Systems and Networks,IEEE Computer Society Press,Los Alamitos,2005:108-117.
[56]Cukier,R.M.a.M.Assessing the Attack Threat due to IRC Channels[C].Proceedings of the 2006 International Conference on Dependable Systems and Networks(DSN’06),Philadelphia,PA,2006:467-472.
[57]李涛.基于免疫的网络安全风险检测[J].中国科学E辑.2005,35(8):798-816.
[58]OSSIM.Open Source Security Information Management[DB/OL].http://www.ossim.net/, 2008.
[59]Wing,J.M.,Manadhata.Measuring a System's Attack Surface[C].Proceedings of the 13th USENIX Security Symposium,San Diego,CA,2004:56-63.
[60]Jonsson,E.,Olovsson,T.A Quantitative Model of the Security Intrusion Process Based on Attacker Behavior[J].IEEE Transactions on Software Engineering,1997 23(4):235-245.
[61]Gehani,A.,Kedem,G.,Rheostat.Real-time Risk Management[C].Proceedings of the 7th Inter-national Symposium on Recent Advances in Intrusion Detection(RAID2004),2004:122-130.
[62]雷英杰.基于直觉模糊推理的态势与威胁评估研究.[D].西安电子科技大学,2005:13.
[63]梅海彬,龚俭.一种基于时间序列面向预警的警报分析方法[J].计算机科学,2007(12):72-76.
[64]Geib,C.W.,Goldman,R.P.Plan Recognition in Intrusion Detection Systems[C]. Proceedings of the DARPA Information Survivability Conference and Exposition(DISCEX II'01),2001:256-266.
[65]Schmidt,C.,Sridharan,N.,Goodson,J.The Plan Recognition Problem:an Intersection of Psychology and Artificial Intelligence[J].Artificial Intelligence,1978(11):45-83.
[66]Kautz,H.,Allen,J.F.Generalized Plan Recognition[C].Proceedings of the Fifth National Conference on Artificial Intelligence,1986:32-38.
[67]Charniak,E.,Goldman,R.P.A Probabilistic Model of Plan Recognition[C].Proceedings of the Ninth National Conference on Artificial Intelligence,1991:160-165.
[68]Qin.X,Lee.W.Attack Plan Recognition and Prediction Using Causal Networks[C].Proceedings of The 20th Annual Computer Security Applications Conference(ACSAC 2004),2004:370-379.
[69]Wang,L.,Liu,A.,Jajodia,S.Using Attack Graphs for Correlating,Hypothesizing,and Predicting Intrusion Alerts[J].Computer Communications,2006(29):2917-2933.
[70]Cunningham,W.H.Optimal Attack and Reinforcement of a Network[J].Journal of the ACM(JACM),1985,32(3):549-561.
[71]Ritchey R W,Ammann P.Using Model Checking to Analyze Network Vulnerabilities[C]. Proceedings of the 2000 IEEE Symposium on Security and Privacy.IEEE Symposium on Security&Privacy.IEEE,2000:156-165.
[72]Sheyner,O.,Haines,J.,Jha,S.,Lippmann,R.,et al.Automated Generation and Analysis of Attack Graphs[C].Proceedings of the 2002 IEEE Symposium on Security and Privacy,2002:273-284.
[73]Hellerstein,J.L.,Ma,S.,Perng,C.-S.Discovering Actionable Patterns in Event Data[J].IBM Systems Journal,2002,41(3):475-482.
[74]Templeton,S.J.,Levitt,K.A Requires/Provides Model for Computer Attacks[C].Proceedings of the New Security Paradigm Workshop.Ballycotton,Ireland,ACM,2001:31-38.
[75]Cuppens,F.,Miege,A.Alert Correlation in a Cooperative Intrusion Detection Framework[C].Proceedings of the 2002 IEEE Symposium on Security and Privacy(SP2002).Berkeley,CA,USA:IEEE Comput.Soc,2002:202-215.
[76]Dain,O.A.C.,R..Fusing a Heterogeneous Alert Stream into Scenarios[C].Proceedings of the 2001 ACM Workshop on Data Mining for Security Applications,2001:372-380.
[77]Lee,W.,Qin,X.Statistical Causality Analysis of INFOSEC Alert Data[C].Poceedings of the 6th International Symposium on Recent Advances in Intrusion Detection(RAID2003):Springer-Verlag,2003:73-94.
[78]Ning P,Cui Y.Techniques and Tools for Analyzing Intrusion Alerts[J].ACM Transaction on Information and System Security,2004,7(2):274-318.
[79]Small Business Innovation Research Program[DB/OL].https://www.dhs.gov/science-and- technology/sbir,2005.
[80]Advanced Research and Development Activity(ARDA)[EB/OL].Exploratory Program Call for Proposals 2006,USA,2005.
